This week at Black Hat conference in Las Vegas, security company Qualys presented and released BlindElephant, a utility that scans web sites for insecure web applications. Their research identified that 70 percent of sites running Drupal are affected by critical vulnerabilities, and that the statistics only get worse for Joomla (92%), MediaWiki (95%), phpBB (100%). 1
I received a press release about BlindElephant earlier this week. At the time, I didn’t think much of it. It surely would have gotten my attention, however, had it included their WordPress statistic — 4 percent. (What did catch my attention was this IDG article.)
The application, the source for which Qualys released, isn’t about identifying critical vulnerabilities; it’s about identifying the versions of software that websites run. They made their own determinations which versions had “critical vulnerabilities.” 2 Check out their slides and white paper, both packed with great information and statistics.
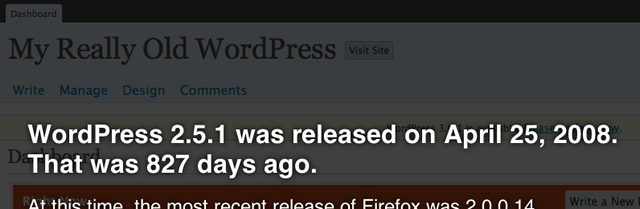
For WordPress, they cited version 2.5.1 as the earliest release outside the critical barrier, which fixed an important security flaw in our secret key implementation.
In case you didn’t already know, that 2.5.1 is not secure. We’ve made countless incremental improvements to the security of WordPress in the four major versions and many maintenance and security releases over last two years.
Alas, WordPress has a security perception issue. It’s widely used and widely targeted. Plugins have extended it every which way. Of course, “My WordPress was hacked!!!!111” doesn’t mean that WP is the attack vector. It very rarely is.
But at the same time, WordPress is easy to use and easy to upgrade. Among major open source web applications, it quite possibly leads in both categories, and its developers and contributors have worked hard to make it that way.
That brings me back to BlindElephant. Their white paper says they checked more than 25,000 WordPress installs and found the vast majority of them to be running WordPress 2.9 or higher. Qualys cited the “application’s easy, reliable updating design” as why we have such a clear advantage. I’m down with that.
WordPress 3.0.1 and beyond
This post’s title comes from the 3.0.1 haiku. If you’re not running 3.0.1, please update. It’s easy, usually always painless, and will provide you (and me) peace of mind. But we do have goals to make it even easier. With that, I leave you with one such proposal, from Daryl Koopersmith (@darylkoop) and me: If you fall behind on your updates, we’re thinking a modal dialog box with a twist. What do you think? 3
Notes:
- The Drupal number may be slightly high, as this comment points out, as Drupal 5.22 may have been incorrectly classified as critical. (Their slides were not kind on Drupal, so I am unsure of the intention.) ↩
- WordPress and Drupal in particular received additional attention of the researchers, as a few dozen popular plugins and modules were also inspected. ↩
- Please know we’re not being serious. We do have plans, but this isn’t it. Well, probably. ↩