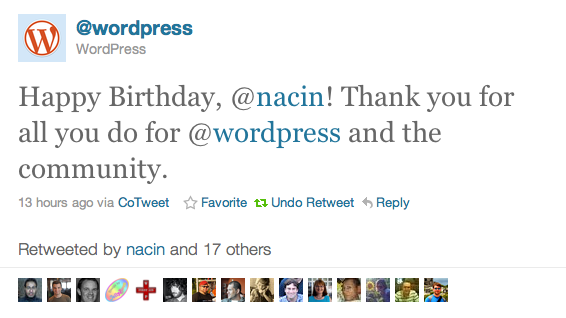
Seriously, does it get cooler than this?
Normally I enjoy the dozens of Facebook wall posts I get on this date every year, many from friends I don’t hear from too often. But there’s something really special about the dozens of mostly random tweets and retweets 1 wishing me a happy birthday and thanking me for my hard work. It makes me feel proud of the work we do and the impact we have doing it.
I only got involved in the WordPress community late last year. A year ago, I could never have imagined where I am now. I love what I do as a core developer. It’s crazy. And it looks like WordPress loves me back, too. Thanks Jane for the tweet, and so many of you in the community for the birthday wishes! 🙂
If you want to pitch a little my way in support my contributions to WordPress, I’ve added a donate page that includes a link to a newly minted but woefully incomplete Amazon wish list.
—
Jane only really thought about doing this recently, but there were two other birthdays in the last two weeks I would be remiss not to mention: good friends and fellow WordPress contributors Daryl Koopersmith and Dion Hulse. I’m now 22, Daryl is 21, Dion is 23, so we’ve got quite a bit ahead of us and I don’t think we’ll be going anywhere anytime soon.
Notes:
- And the new followers courtesy of the @wordpress account’s 77,000 followers! 🙂 ↩